In the landscape of forever changing threats, one that is always overlooked is the FTP service running on machines.
In Windows 11, this is no different to legacy versions that were running FTP. As a simple exercise, I installed a Windows 11 machine, this machine is vanilla, meaning it has none of the items below:
- No Anti-Virus
- No Group Policy
- Not domain joined
- No restrictions
Installation/Configuration
To enable FTP on Windows 11, I went over to Control Panel and then clicked on Programs & Features and then on the left-hand side, I selected the option to turn windows features on or off which brings up the window below:
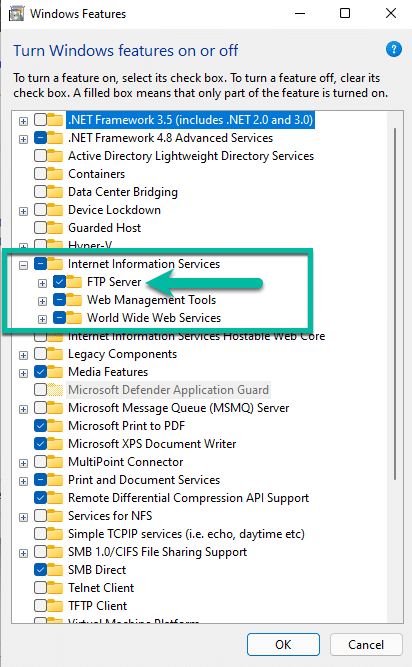
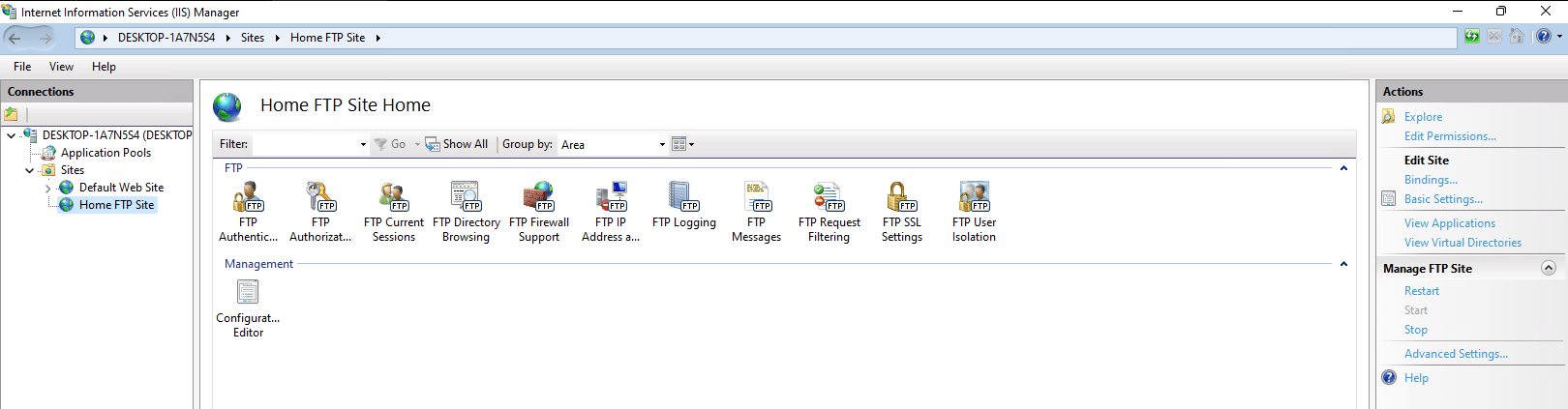
I enabled FTP and its extensions under IIS and then let it install. Once installed, I headed over to IIS (Internet Information Services) and created an FTP site and pointed it to the INETPUB directory and once setup, it looked like the below figure:
Kali Linux
Now that FTP and IIS were running, it was time to run a few simple Kali Linux tools to see what we can find, obviously FTP is our interest here but these are the tools used in this exercise:
- NMAP
- Nessus
- Terminal
NMAP
I ran a lengthy NMAP scan to see what it came back with on Windows 11 and below is the final output from NMAP:
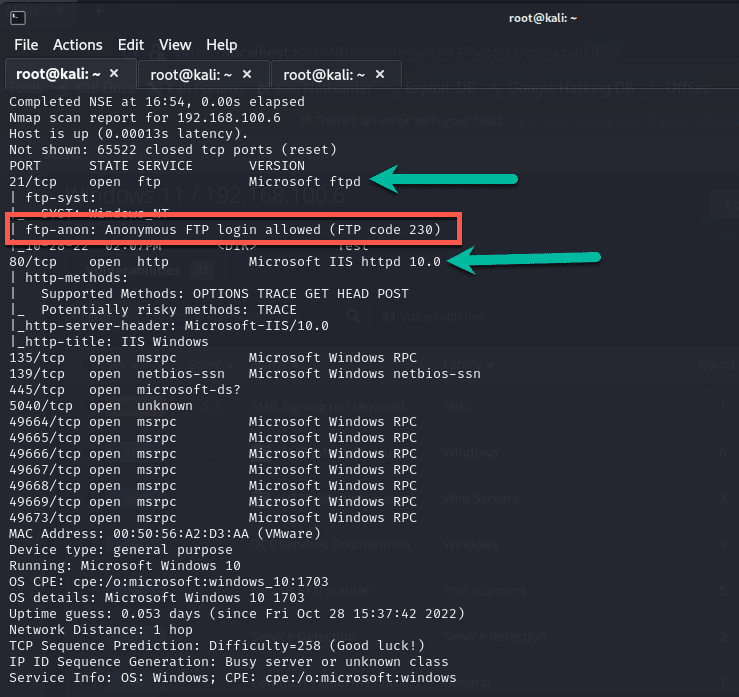
It listed the FTP port which is what we wanted to achieve and would show up in the scan regardless but what I wanted to point out is that because I just threw this install in here, I didn’t take precaution to ensure it was locked down and NMAP pointed it out showing that anonymous FTP is enabled.
This means an attacker can have a ball with this by uploading or downloading files. I am not going to deep dive ethical hacking as there are many courses out there for that.
We can also see that ports 80,139,445 etc. are open and can also pose a threat if exploited.
Nessus
Another great tool used in this exercise was Nessus. After selecting a basic scan with the defaults, it came back with a medium vulnerability along with some informational alerts and the one again we wanted which was FTP.
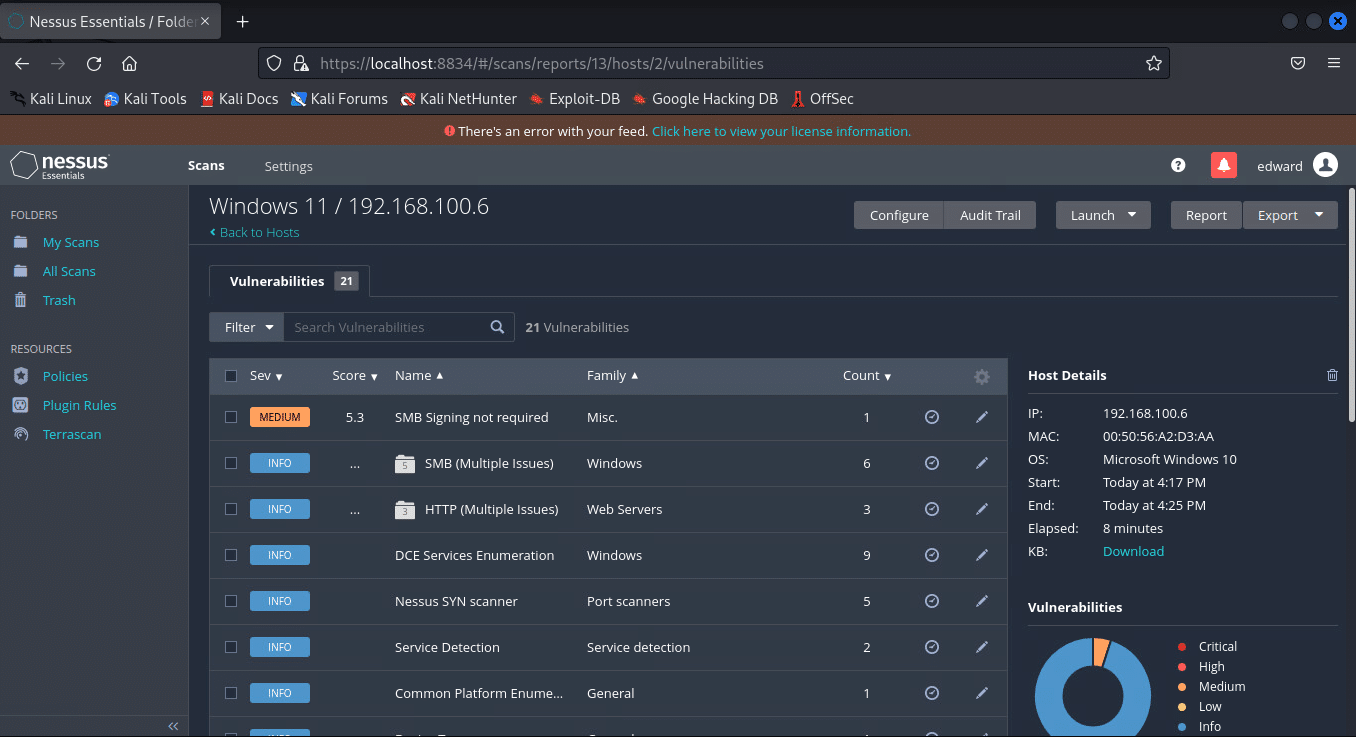
FTP section:
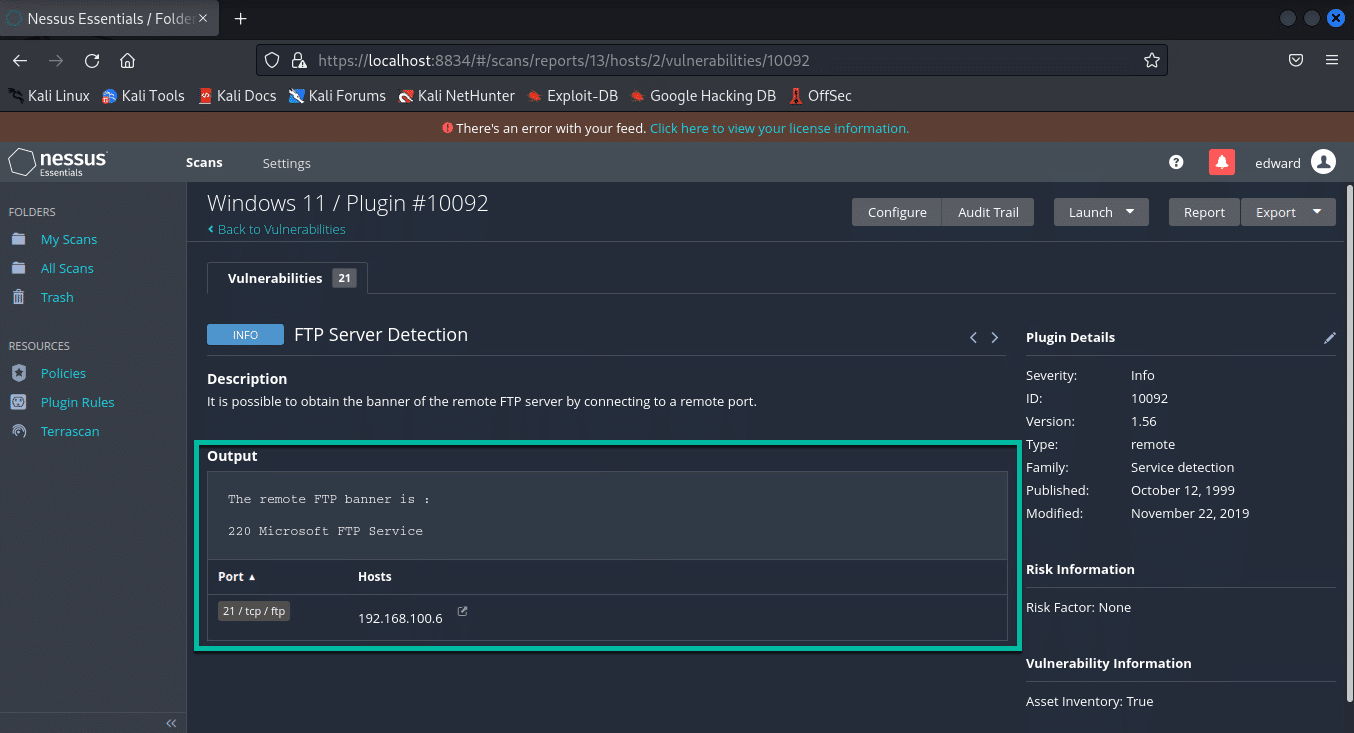
Terminal
The final test I did was using the Terminal and running a simple command such as shown in the figure below:
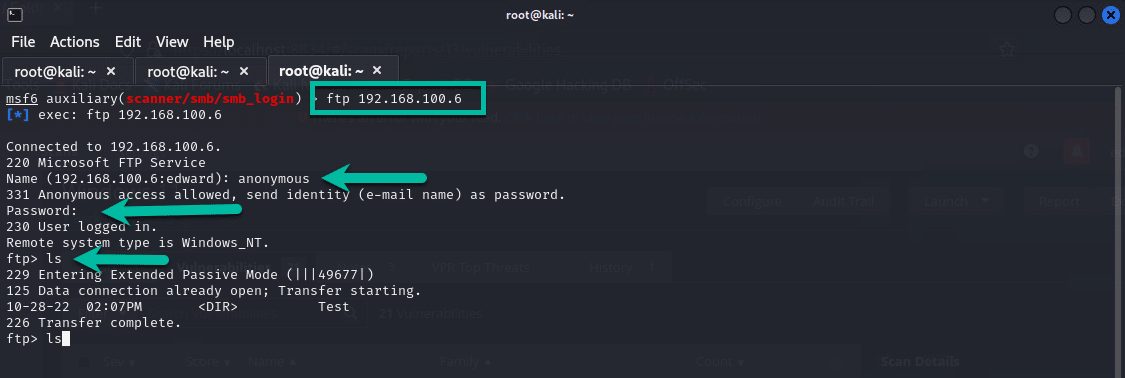
Using ftp 192.168.100.6 which is the IP of my Windows 11 machine, I logged in using Anonymous as both the username and password.
After I got a successful login, I ran the ls command to show any files or folders and we could see a folder called Test. Inside Test I had a text file and running another ls command I was able to see this and finally, ran a get command to download the file as shown in the figure below:
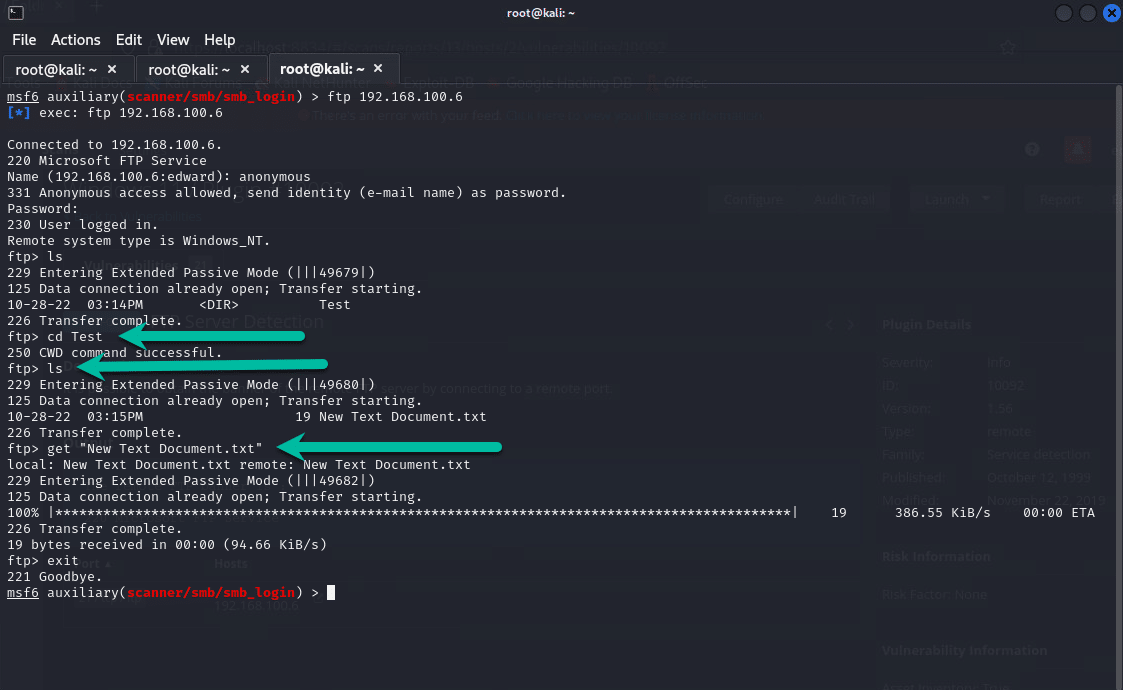
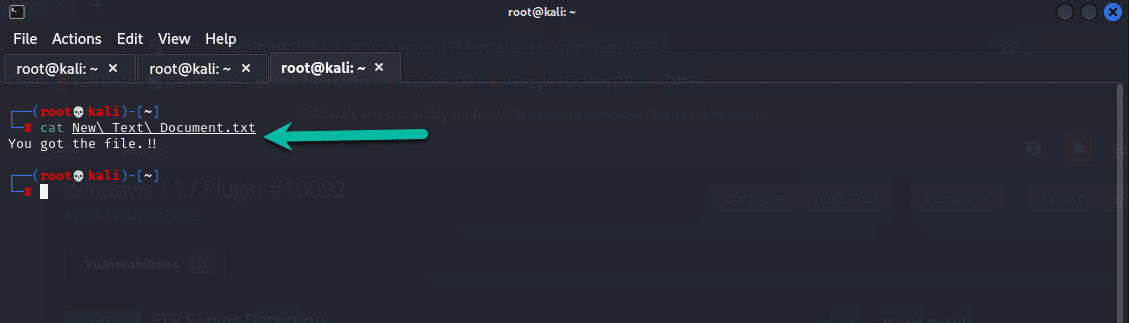
Finally running a cat command I could see the content of the text file I downloaded as shown below.
Many admins or users place sensitive in FTP sites and this can include usernames or passwords, location to files, other system information, banking information etc.
Conclusion
You may be thinking to yourself, you did all this and got access because you were logged into the machine etc. Right!, but, let’s say you published this information to the internet. A quick scan would have revealed all the information like I have shown you above to an attacker and the experienced attackers would take this further to get into the environment and exploit things further.
An attacker that gained access to your environment can do the exact same thing after initial exploitation of a machine.
Just because we have a newer operating system such as Windows 11, does not mean we should let our guard down. FTP is still vulnerable just like it is in other versions of Windows. Before publishing something, make sure you have taken the time to lock down the application or service and only allow access where it is needed.
As a final test, I installed ESET and then Symantec and both alerted of a possible attack when I ran scans on the network. This would have alerted IT that something is happening in the network so be sure that you have IDS/IPS and your machines are secure. Data is valuable and should be kept safe along with your end users.
Hope it helps.