In my blog post yesterday where I show cased that a bad actor can get the Exchange Server version with CU/SU you are running and based on that information if not patched start attacking your server.
In the October 2023 Security Update for Exchange, KB5030877 for both Exchange Server 2016 and Exchange Server 2019, a CVE is addressed in this update along with some other fixes.
The important part is ensuring that you apply the patch to close the vulnerability. To read about this update and to download it, head over to the link below:
The CVE addressed in this update is CVE-2023-36778 and the Microsoft MSRC website gives the CVSS score along with an explanation of the vulnerability, you can read about it here:
https://wwwmsrc.microsoft.com/update-guide/vulnerability/CVE-2023-36778
Applying the update
As with any other update, running the Security Update (SU) can be done from an elevated command prompt, here are a few screenshots of the actual install:
Sometimes you will be prompted to reboot, I have had on a few occasions that the installer just exists back to the command prompt but was successful and you have to manually reboot.
You can check that it is installed as per the first article with the health checker.
Post check for any exploitation
In my blog post below, you can see in NMAP that the CVE listed above was shown and that the server was vulnerable but in the image of NMAP (Zenmap – Windows Version) listed below the blog post, you can see that no CVE is listed after apply this Security Update.
Zenmap scan with no CVE listed:
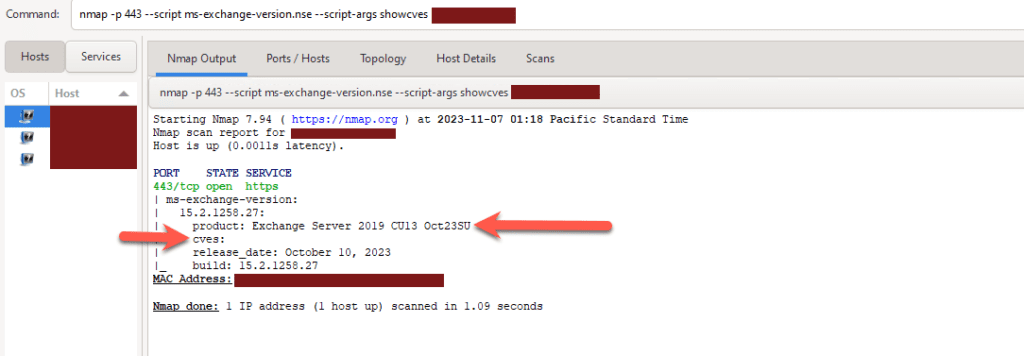
Why am I showing you this, to make you aware that bad actors are constantly looking for systems to exploit, by patching, you ensure that your environment is secure from this threat.
Keep your systems patched, this not only applies to Microsoft Exchange Server but everything you run in your environment.
Happy Patching!
