Microsoft released V2 of the August Security Update for Exchange 2019 which includes an extra step that addresses a vulnerability.
In this blog post, we will cover the following:
- Quick overview of Exchange 2019 CU13 install
- Quick overview of applying the Security patch (V2) for Exchange Server 2019
- CVE-2023-21709 PowerShell script execution
Exchange 2019 CU13 Installation:
If you are running Exchange 2019 on Windows Server core like I am in my lab, you do not have a GUI to double click the ISO and run it. You need to use PowerShell to mount the ISO file and then access the Drive letter.
The installation files are on the server and we need to navigate to that folder. You can now use the following command to not only mount the Exchange 2019 ISO but also get the letter assigned to it without having to navigate through the alphabet.
Firstly, from server core, remember to type in “PowerShell” (without the quotations) and hit enter or the command won’t work in command prompt.
- Mount-DiskImage “Path.ISO” | Get-Volume
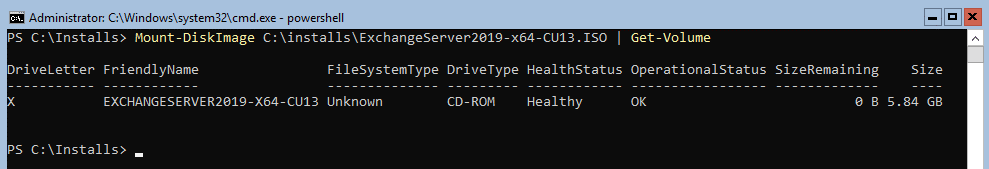
Once it completes as shown above, we can execute the install from command line. Remember if you are new to this kind of install, the License terms have been updated to include DiagnosticDataON or Off. Your command can be as follows, the mode will obviously change if you are installing and you will also have the /role option:
- .\Setup.exe /IAcceptExchangeServerLicenseTerms_DiagnosticDataON /Mode:Upgrade
Once you run the command, depending on how powerful your server is, the setup can take a while, below is the completion of my setup:
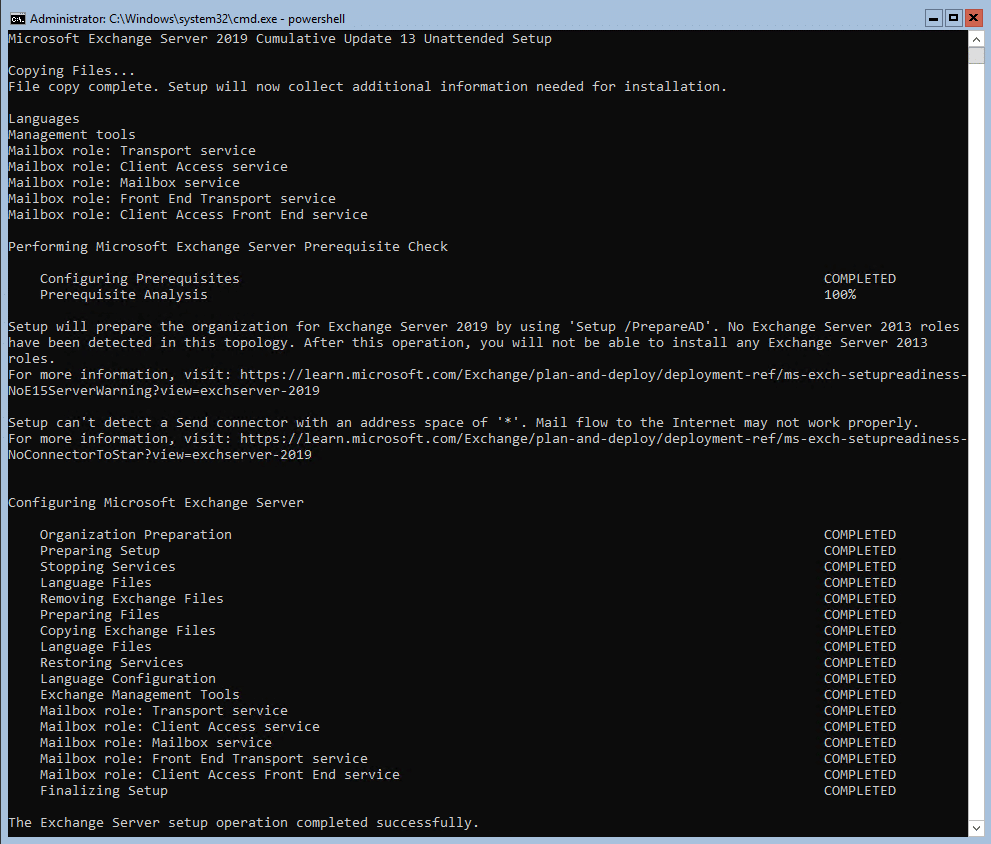
We need to reboot the server so we can move to step 2 of applying the security update.
Exchange 2019 CU13 Security update:
I normally run this from an elevated command prompt vs using a right-click and Install. Below are the steps shown during the installation of the security update:
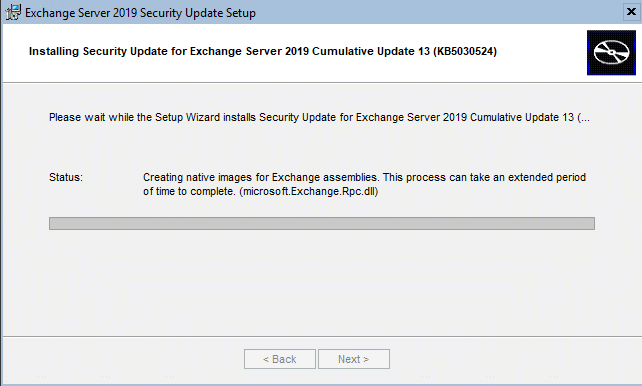
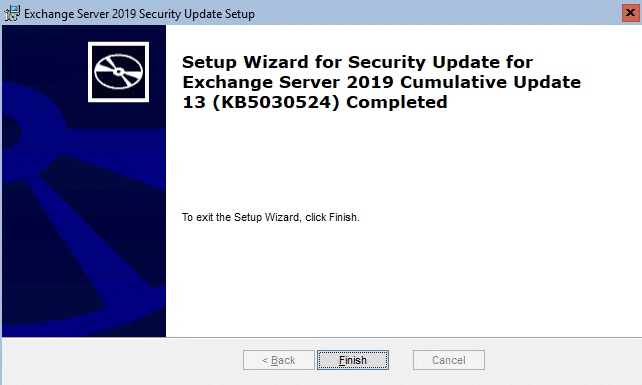
Now that the CU and SU have been covered, we can click Finish and at the prompt restart the Exchange 2019 server. Now we can move onto addressing the CVE.
CVE-2023-21709 PowerShell execution
In the tech community article below, Microsoft advise what you need to do to address this CVE in question.
If you head over to the GitHub page below, you can download the script and also view all the options available:
https://wwwmicrosoft.github.io/CSS-Exchange/Security/CVE-2023-21709/
Below is a snippet of the script that ran. You need to load PowerShell on Server Core or if you using a GUI then launch it elevated.
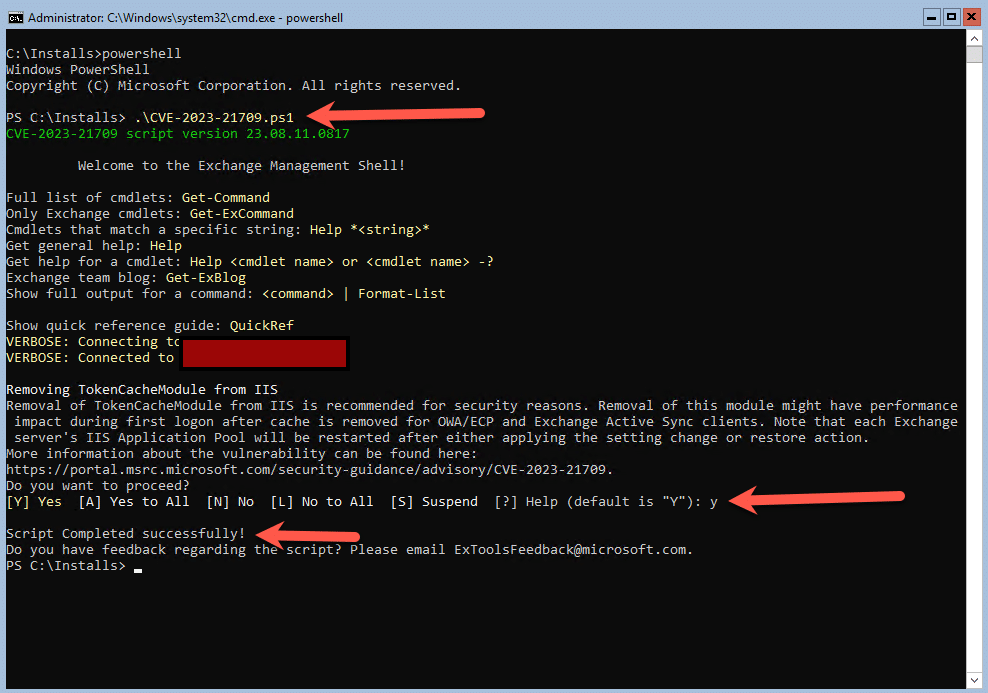
The script executed successfully after removing the TokenCacheModule from IIS. I rebooted the server and have not noticed anything out the ordinary, however this is a lab server and production servers can have additional impact, you will need to monitor it before rolling it out.
Read the two articles and patch your servers.
Hope it helps.
