Performing some tests against my lab Exchange servers, I noticed that Shodan.io revealed information. Take note that attackers also use Shodan.io when enumerating targets.
After digging further with NMAP and some scripts, it became more apparent that internal information was being shown.
The NMAP scan I used was a simple one that used one of the NMAP scripts:
nmap -p 25 --script smtp-ntlm-info <IP>This is what was revealed by NMAP:
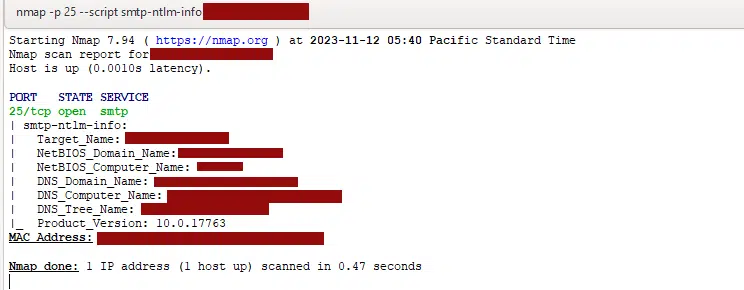
Target_Name: Exchange_info
NetBIOS_Domain_Name: Exchange_info
NetBIOS_Computer_Name: Server1
DNS_Domain_Name: Exchange_info.local
DNS_Computer_Name: server1.Exchange_info.local
DNS_Tree_Name: Exchange_info.local
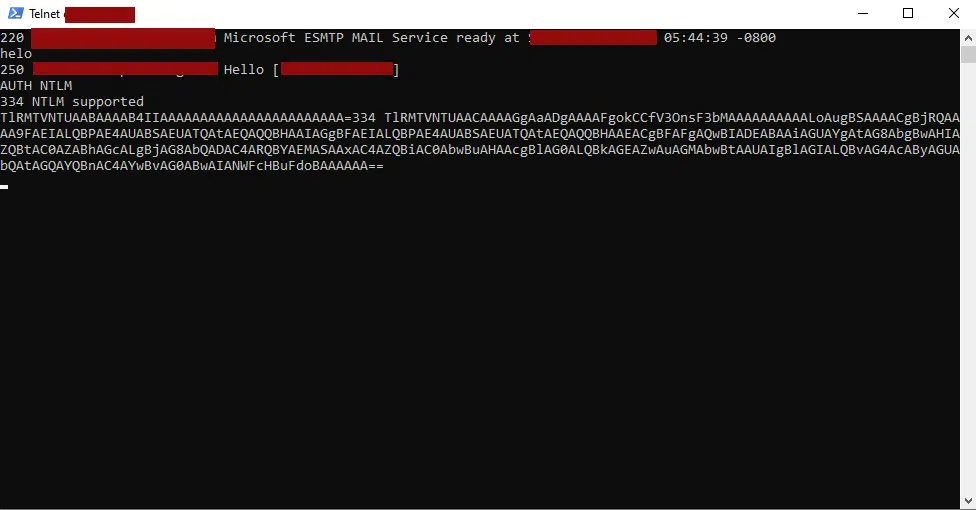
I then used Telnet to perform the same kind of check and this was the results where I received a challenge response:
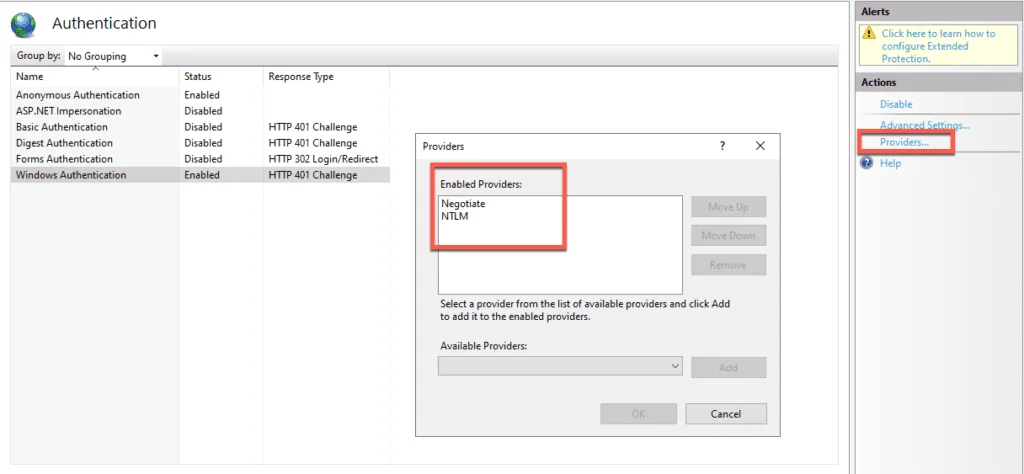
If we open up IIS Manager and you head over to the site -> Authentication and then you click on Windows Authentication, you should see the providers option on the right-hand side if Windows Authentication is enabled, you can change the providers by removing NTLM for example and then from the drop-down where it lists “available providers”, select the new one and then press Add.
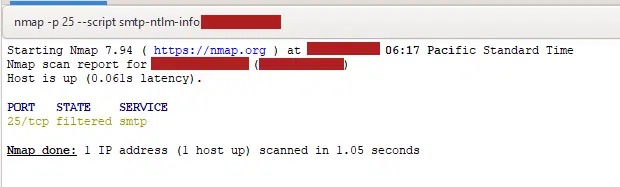
Obviously this is a lab and I can break/fix things but I did not make any changes. I do not think you can hide this information with IIS but more filtering port 25 so its not “open” but “filtered” on the internet like shown below, where you cannot see any information:
The more information attackers have, the better they can try and map out things or attack your environment. Keep your information safe.
Hope it helps.
