NMAP and NMAP scripting Engine
Introduction
Nmap, short for Network Mapper, is a powerful and versatile open-source network scanning tool used for security auditing and network exploration. It allows users to discover hosts, services, and vulnerabilities on a network, making it an essential tool for network administrators, security professionals, and ethical hackers.
Using Nmap
Nmap is a command-line tool, available for various operating systems, including Windows, Linux, and macOS. Here are the basic steps to use Nmap:
Step 1: Install Nmap
First, you need to install Nmap on your system. If you are running Kali Linux, this should be installed for you by default.
If you are using a Windows OS, you can use Zenmap.
You can download the latest version from the official Nmap website (https://nmap.org/).
Step 2: Launch Nmap
Open a terminal on Kali Linux or launch Zenmap from your Windows Operating system. You can also search Kali Linux for Nmap, here is the Icon of what it looks like:

Step 3: Basic Scan
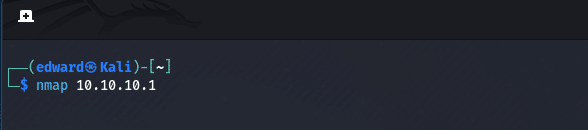
To perform a basic scan, use the following command:nmap target
Replace “target” with the IP address or hostname of the target you want to scan. For example:nmap 192.168.0.1
Step 4: Advanced Scanning Techniques
Nmap offers a wide range of scanning techniques and options to tailor your scan according to your needs. Here are some commonly used options:
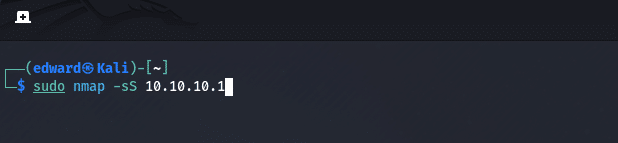
1. TCP SYN Scan
nmap -sS target
The TCP SYN scan is the default scan type in Nmap. It sends SYN packets to the target’s ports and analyzes the response to determine if the port is open, closed, or filtered. This command will need to run as Root.
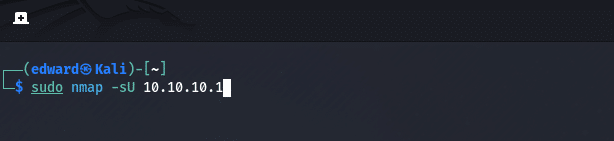
2. UDP Scan
nmap -sU target
UDP scans are used to identify open UDP ports on a target. UDP scans are slower than TCP scans because UDP is a connectionless protocol.
3. OS Detection
nmap -O target
Nmap can attempt to identify the operating system running on the target by analyzing various network characteristics and responses.
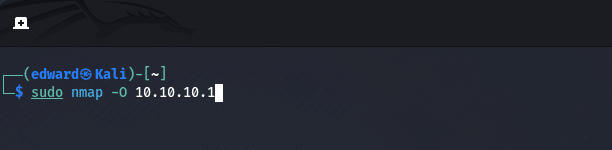
4. Service Version Detection
nmap -sV target
This option enables Nmap to identify the version and type of services running on open ports.
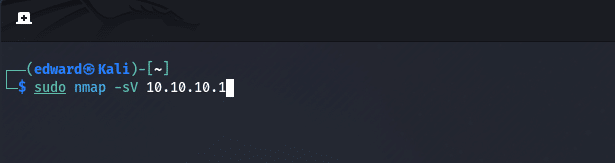
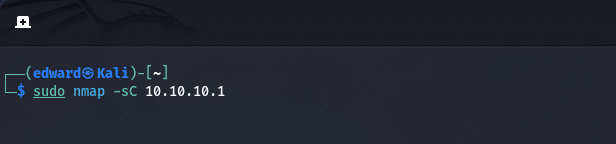
5. Script Scanning
nmap -sC target
Nmap has a built-in scripting engine that allows users to write and execute scripts to automate tasks or perform advanced scanning techniques. We will explore the Nmap Scripting Engine in the next section.
The Nmap Scripting Engine
The Nmap Scripting Engine (NSE) is a powerful feature of Nmap that enables users to automate tasks, perform advanced scans, and gather additional information about the target network. Here are some key points about the NSE:
1. Script Categories
The NSE scripts are organized into different categories, such as default, discovery, brute, exploit, and more. Each category contains scripts related to specific tasks.
2. Running NSE Scripts
To run NSE scripts, use the following command:nmap –script <script-name> target
Replace “<script-name>” with the name of the script you want to execute. For example:nmap –script http-title 192.168.0.1
3. Script Output
NSE scripts provide detailed output, including information about discovered vulnerabilities, service versions, and more. You can customize the output format using options like --script-args and --script-trace.
4. Script Development
If you want to develop your own NSE scripts, you can find the NSE script development guide on the official Nmap website.
List of Nmap Command Options
Here is a comprehensive list of Nmap command options:
Scan Techniques:
- -sS: TCP SYN scan
- -sT: TCP connect scan
- -sU: UDP scan
- -sA: TCP ACK scan
- -sN: TCP NULL scan
Host Discovery:
- -sn: Ping scan
- -Pn: Treat all hosts as online
- -PR: ARP ping scan
Output Options:
- -oN: Output to normal format
- -oX: Output to XML format
- -oG: Output to grepable format
Timing and Performance:
- -T0 to -T5: Timing templates
- -max-rtt-timeout: Maximum RTT timeout
- -min-rtt-timeout: Minimum RTT timeout
Scripting Engine:
- –script: Run NSE scripts
- –script-args: Set arguments for NSE scripts
- –script-trace: Show detailed script execution trace
Other Options:
- -v: Increase verbosity
- -A: Enable OS and version detection
- -p: Specify ports to scan
These are just a few examples of the numerous command options available in Nmap. Refer to the Nmap documentation for a complete list of options and their usage.
Conclusion
Nmap is a versatile and powerful network scanning tool that provides valuable insights into network security. By understanding the basic usage of Nmap and exploring the capabilities of the Nmap Scripting Engine, you can enhance your network auditing and exploration processes. Remember to use Nmap responsibly and with proper authorization.